Blog
Case studies, strategies, and ideas shaping modern technology.
Nginx Case Study
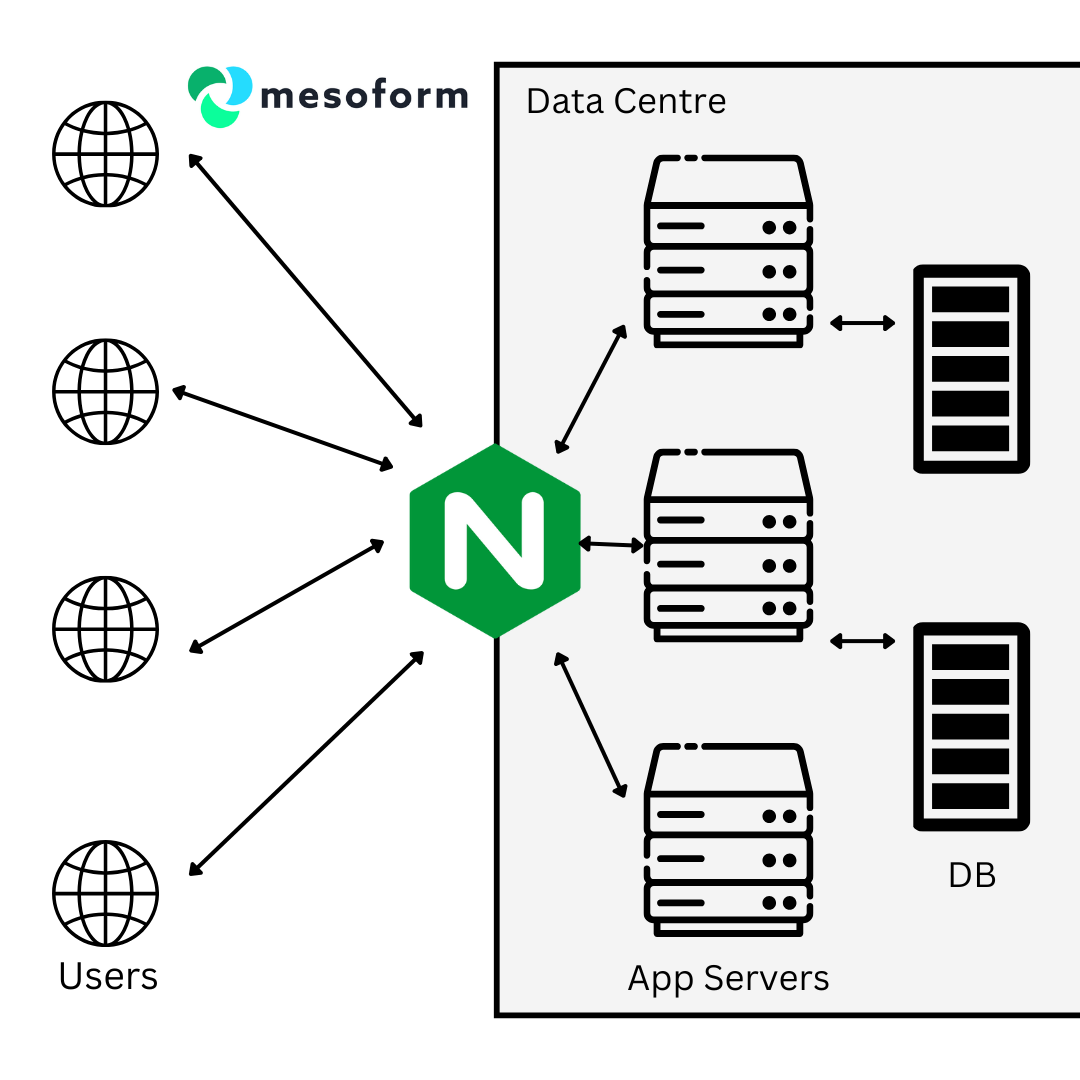
This blog is on the importance of NGINX and will discuss how Mesoform implemented it despite facing challenges. Making use of multiple technologies to secure your IT.
The main benefits of using NGINX packages from your vendor are:
- Simple and straightforward configuration: NGINX packages from a vendor typically come with preconfigured settings that are optimized for specific use cases. This makes it much easier for users to install and set up NGINX, even if they don't have a lot of experience with the software. Additionally, these preconfigured settings often include best practices for security and performance, which can help users avoid common pitfalls.
- Dependency resolution: NGINX has a number of dependencies that must be installed and configured correctly in order for it to function properly. When you use NGINX packages from a vendor, the vendor has already taken care of ensuring that all dependencies are installed and configured correctly. This can save users a lot of time and frustration.
- Increased effectiveness of maintenance and security patches: NGINX is a popular web server software that is frequently updated with maintenance and security patches. When users install NGINX packages from a vendor, they can be sure that they are receiving the most up-to-date version of the software, along with any necessary patches. This can help ensure the security and stability of their web servers. Additionally, vendors often provide their own support and assistance for their packages, which can be a valuable resource for users who encounter issues with their NGINX installations.
Despite its advantages, all apps should be secured when running on the Internet. A few high-level examples would be:
- Always ensure you install Nginx from a reputable and verified source: One of the most important steps in securing an app running on the internet is to make sure that the software is obtained from a trusted source. This is particularly important when it comes to Nginx, as the software is often used as a web server and therefore has access to sensitive information. By installing Nginx from a reputable and verified source, users can be sure that they are receiving the legitimate software and that it has not been tampered with or modified in any way.
- Use an installation method which allows you to eliminate unwanted modules. Even if it means building from source code: Nginx is a modular software, which means that it can be customized by adding or removing modules. However, not all modules are necessary for every use case, and some may even introduce security vulnerabilities. By using an installation method that allows users to eliminate unwanted modules, they can reduce the attack surface of their Nginx installation and minimize the risk of exploitation. Building from source code is one method that allows for this level of customization.
- Disable server tokens because they disclose unnecessary information about the server which could help a bad actor with targeted attacks: Server tokens are pieces of information that are included in server responses, and they can provide clues about the software and version running on the server. This information can be useful to attackers who are attempting to exploit known vulnerabilities in specific software versions. By disabling server tokens, users can reduce the amount of information that is disclosed about their server and make it more difficult for attackers to target their software. This can be done by setting the "server_tokens" directive to "off" in the Nginx configuration file.
Nginx Compression:
NGINX can compress responses to improve delivery speed and reduce overhead on the server. Compressing responses often significantly speeds up app/webpage response times.
However, compression has been linked with the a number of vulnerabilities. For example:
Breach Attack: The Breach attack is a vulnerability that exploits the way in which compression is used in HTTPS communication. The attack allows an attacker to infer the content of encrypted data by analyzing the size of the compressed responses sent by the server. This can be used to steal sensitive information such as session cookies, login credentials, and other data. The Breach attack was first reported in 2013 and affected a number of popular websites that used HTTPS with compression.
Zip Slip Vulnerability: The Zip Slip vulnerability is a security issue that affects applications that handle compressed archives such as ZIP, TAR, and JAR files. The vulnerability allows an attacker to exploit a directory traversal vulnerability in the extraction process of a compressed archive to execute arbitrary code on the target system. This can lead to serious consequences such as data theft, system compromise, and other attacks.
To address these vulnerabilities, it is important to properly configure and secure your web server and application. For example, you can disable compression if it is not required, ensure that you are using the latest version of your web server and application, and implement other security measures such as access control and input validation to prevent attacks. Additionally, it is important to stay up-to-date with the latest security vulnerabilities and patches to ensure that your web application remains secure.
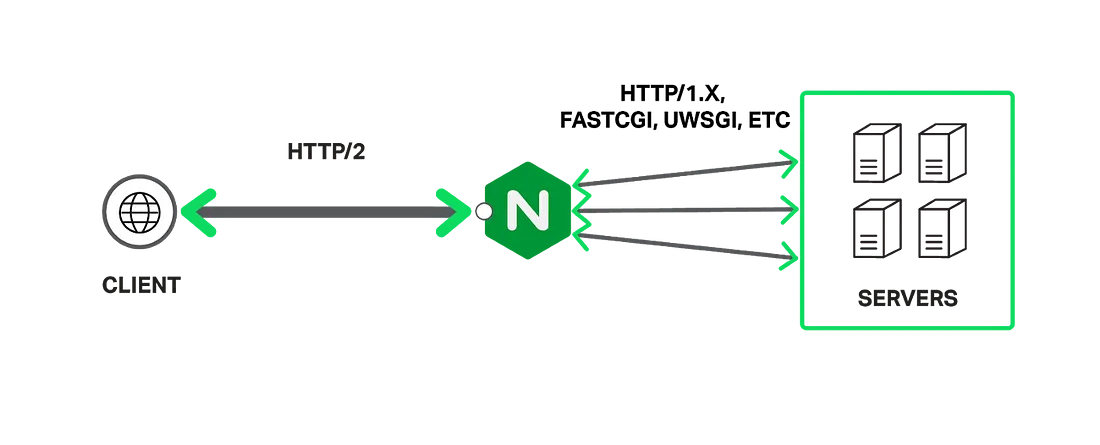
What would Mesoform do?
- We always compile Nginx from the source code so that we have high confidence in the build.
- Building from source also allows us to ensure gzip modules are not even installed when the Nginx is running. Leaving no opportunity for misconfiguration.
- We will then remove any other modules which the app running on the web server doesn't need.
Restricting HTTP Methods
The purpose of configuring an Nginx server to only allow specific HTTP methods is to improve the web application's security. By restricting the HTTP methods allowed for a particular location, you can prevent attackers from exploiting vulnerabilities specific to certain HTTP methods. For example...

Preventing exploitation of vulnerabilities: By allowing only a subset of HTTP methods, you can prevent attackers from exploiting known vulnerabilities that are specific to certain HTTP methods. For example, the HTTP TRACE method can be used by attackers to steal sensitive information such as session IDs, cookies, and other credentials. By disabling the TRACE method, you can prevent this type of attack.
Limiting attack surface: By limiting the HTTP methods allowed for a particular location, you are essentially reducing the attack surface that an attacker can exploit. This can be particularly useful if your web application is designed to only handle a specific set of HTTP methods. For example, if your application is designed to handle only GET and POST requests, you can disable all other HTTP methods to reduce the likelihood of an attacker exploiting a vulnerability.
Examples of HTTP methods:
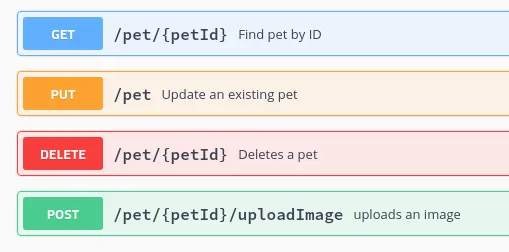
What would Mesoform do?
Recently Mesoform used this feature to block PUT and DELETE methods from being sent to a client's application deployed on Nginx and running in Google Cloud Run. This immediately reduced the attack surface because any vulnerabilities which leverage these methods are immediately off-limits to attackers.
Mesoform offers secure deployments and training for our clients at a lower overall development cost due to our extensive experience building and running web servers.
If you would like to discuss any of these topics in more detail, please feel free to get in touch

