Blog
Case studies, strategies, and ideas shaping modern technology.
Technology Musings Episode 9

In this edition of Tech Musings, we will delve into the world of cybersecurity, exploring a few useful security decisions we recommend to our valued clients and some future trends and predictions we see in the industry. In an increasingly interconnected digital landscape, protecting sensitive data and safeguarding online assets have become paramount for individuals and organisations alike. With cyber threats evolving at an alarming rate, making informed security choices is no longer optional - it's a necessity.
Cloud Encryption
First and foremost, we need to mention Cloud encryption. Encryption is a critical security measure that helps protect sensitive data stored in the cloud from unauthorised access. When data is encrypted, it is transformed into an unreadable format, ensuring that even if an attacker gains access to the encrypted data, they cannot decipher its contents without the encryption key. This is essential when operating on the Cloud. Remember, Cloud infrastructure is public infrastructure, so you should always work in a mode of zero trust.
Why it Matters:
- Data Privacy: Encryption ensures that data remains private and secure, even if it is stored or transmitted across untrusted networks or resides on shared infrastructure in the cloud. It prevents unauthorised parties, including cloud service providers, from accessing and viewing sensitive information.
- Compliance Requirements: Many industries and jurisdictions have specific data protection regulations and compliance standards. Encryption helps meet these requirements by providing an additional layer of security for sensitive data. For instance, regulations such as the General Data Protection Regulation (GDPR) mandate the protection of personal data through encryption.
- Data Breach Mitigation: In the event of a data breach or unauthorised access, encrypted data is significantly more challenging for attackers to exploit. Encryption acts as a safeguard, reducing the risk of data exposure and limiting the potential damage caused by a breach.
Things to consider:
- Identify Sensitive Data: Determine which data requires encryption based on its sensitivity, regulatory requirements, and potential impact if compromised.
- Choose an Encryption Approach: There are different encryption methods to consider, such as symmetric encryption (using the same key for encryption and decryption) or asymmetric encryption (using a public-private key pair).
- Utilise a Hardware Security Module: (HSMs are specialised hardware devices) or a secure key management service to securely store and manage the keys. Both are usually offered by your Cloud provider.
- Encryption at Rest: Encrypt data stored in the cloud. Most cloud service providers offer native and integrated encryption features to do this. Alternatively, you can encrypt data on the client-side before uploading it to the cloud. Offered by default on Google Cloud but not on other providers
- Encryption in Transit: Encrypt data during transmission between your local systems and the cloud provider using secure protocols like HTTPS, SSL/TLS, or VPN tunnels. Ensure that your cloud provider supports strong encryption for data transmission and follow their recommendations for configuring encryption protocols. Google Cloud offer this on all their services as do the other major providers
- Identity and access management: Implement strict access controls to limit who can access the encrypted data by applying strict access controls to limit key access to authorised personnel only. Implement role-based access control (RBAC) to ensure that users only have access to the keys they need for their specific tasks.
- Auditing and Monitoring: Implement mechanisms to monitor and log access to encrypted data. Regularly review audit logs and who has what access to detect any suspicious activity or potential security risks.
- Incident Response and Recovery: Develop an incident response plan outlining steps to be taken in case of a security incident or data breach. Include procedures for recovering encrypted data and investigating the root cause of the incident.
Source: Spiceworks
Multi-Factor Authentication
Multi-Factor Authentication (MFA) plays a crucial role in enhancing cloud security. As organisations increasingly rely on cloud services for data storage, application hosting, and other critical operations, it becomes essential to implement robust security measures to protect sensitive information. MFA provides an additional layer of defence against unauthorised access and helps mitigate the risks associated with compromised credentials.
Why it Matters:
- Stronger User Authentication: MFA adds an extra layer of authentication beyond the traditional username and password combination. Typically, it requires users to provide at least two or more factors of authentication, such as something they know (password), something they have (a mobile device or token), or something they are (biometric data like fingerprints or facial recognition). By combining multiple factors, MFA significantly strengthens the authentication process and reduces the chances of unauthorised access even if one factor is compromised.
- Protection Against Credential Theft: One of the most common security threats is credential theft, where malicious actors gain unauthorised access by stealing or guessing user passwords. With MFA, even if an attacker manages to obtain a user's password, they would still need the additional factors to successfully authenticate. This greatly reduces the effectiveness of credential theft attempts and provides an additional barrier against unauthorised entry.
- Mitigation of Phishing Attacks: Phishing attacks are a prevalent method used by attackers to trick users into revealing their login credentials. By impersonating legitimate websites or sending deceptive emails, attackers attempt to collect sensitive information. MFA helps combat phishing attacks because even if a user falls victim to a phishing attempt and enters their credentials on a fake site, the attacker would still be unable to access the account without the additional authentication factors.
- Compliance Requirements: Many industries and regulatory frameworks have specific requirements for securing sensitive data. MFA is often mandated as a security control in various compliance standards, such as the Payment Card Industry Data Security Standard (PCI DSS), the Health Insurance Portability and Accountability Act (HIPAA), and the General Data Protection Regulation (GDPR). Implementing MFA helps organisations meet these requirements and demonstrates a commitment to data security and privacy.
- Enhanced Security for Remote Access: Cloud services enable remote access to data and applications, which can increase the risk of unauthorised access. MFA adds an extra layer of security for remote users, ensuring that only authorised individuals can access cloud resources, even if they are connecting from outside the organisation's network.
- Safeguarding Against Insider Threats: Insider threats, where authorised individuals abuse their privileges, can pose a significant risk to cloud security. MFA makes it more challenging for insiders to compromise accounts or perform unauthorised actions since they would need to bypass additional authentication factors. It acts as a deterrent and provides an additional control to mitigate the risks associated with insider threats.
Things to consider:
- Choose MFA Methods: Decide on the MFA methods you wish to support. Common MFA methods include:
- One-Time Passwords (OTP): Generated by an authenticator app like Google Authenticator or sent via SMS (prefer MFA apps as they are more difficult to port elsewhere and also have additional biometric authentication to open them).
- Push Notifications: Users receive a push notification on their registered mobile device to approve or deny login attempts.
- Biometrics: Fingerprint, facial recognition, or iris scanning. Passkeys are a new technology which allow these local technologies to be used on remote services.
- Physical Tokens: Smart cards, USB security keys (like YubiKey), or hardware tokens.
- Integrate MFA into your Application or System:
- If you're using an existing application or service, check if it supports MFA. Many popular platforms provide built-in MFA options that you can enable for users.
- If you're building a custom application, consider using third-party libraries or services that handle MFA for you. This can save time and ensure best practices are followed.
- User Registration and Enrolment:
- During the user registration process, prompt users to set up MFA. This may involve asking them to provide a phone number, install an authenticator app, or register a hardware token.
- Ensure the enrolment process is user-friendly and provides clear instructions for setting up MFA.
- Secure Storage of MFA Information:
- Take extra precautions to secure the MFA information associated with each user account. Use strong encryption and access controls to protect this sensitive data.
- Authentication Workflow:
- When a user tries to log in, request their primary credentials (usually a username and password).
- If the primary credentials are correct, prompt the user for the second factor (e.g., OTP, biometric scan, or approve/deny push notification).
- Only grant access if both factors are successfully verified.
- Fallback Options:
- Provide a backup method for users who may not have access to their primary MFA method (e.g., backup codes, SMS, or email recovery).
- Periodic MFA Re-authentication:
- For sensitive applications, consider requiring periodic re-authentication, especially for sessions that last a long time.
- User Communication and Training:
- Inform users about the importance of MFA and how to set it up correctly.
- Provide clear instructions on how to use MFA and what to do if they lose access to their MFA device or encounter issues.
- Monitoring and Auditing:
- Monitor MFA usage and login attempts for any suspicious patterns.
- Regularly audit MFA settings and review access logs. Often services will enable or improve their MFA settings after first being set-up
Source: Avatier
DDoS attacks
DDoS (Distributed Denial of Service) attacks pose a significant threat to cloud infrastructure due to their potential for misuse. In a DDoS attack, multiple compromised devices or botnets flood a target system or network with a massive volume of traffic, overwhelming its resources and causing a denial of service for legitimate users. Despite some popular beliefs, DDoS attacks are a still significant threat on and from Cloud infrastructure due to the nature of how Cloud is designed to work.
Why it Matters:
- Scalability: Cloud platforms offer high scalability, allowing attackers to rent or compromise a large number of virtual machines or instances to launch DDoS attacks with significant traffic volume. The vast resources available in the cloud make it easier to generate a massive amount of traffic and amplify the attack's impact.
- Bandwidth: Cloud providers typically offer high bandwidth connectivity, enabling attackers to leverage the cloud infrastructure's robust network to deliver a substantial volume of traffic to the target. This can result in severe disruptions and downtime for the victim's systems and services.
- Pay-as-You-Go Model: Cloud services often operate on a pay-as-you-go model, where customers are charged based on resource usage. Attackers can take advantage of this model by utilising stolen credentials or exploiting vulnerabilities to launch DDoS attacks, leaving the financial burden on the victim or unsuspecting cloud account owner.
- Multi-Tenancy: Cloud environments are designed to host multiple customers or tenants on shared infrastructure. If one tenant within the cloud is targeted by a DDoS attack, it can potentially impact the performance and availability of other tenants sharing the same underlying resources.
- Reputation: If you are the victim of a DDoS attack by either someone DDoSing you or hijacking your infrastructure and using it to DDoS someone else, you risk significant impact to your companies reputation and could even risk being shutdown by your Cloud provider.
Things to consider:
- DDoS Protection Services: Cloud providers typically offer DDoS protection services as part of their offerings. These services employ various techniques, such as traffic monitoring, rate limiting, traffic filtering, and automated mitigation, to detect and mitigate DDoS attacks in real-time.
- Application and Infrastructure Security: Implement robust security measures within your cloud environment, including firewalls, intrusion detection and prevention systems (IDPS), and web application firewalls (WAFs). Regularly patch and update your systems and applications to address any vulnerabilities that could be exploited for DDoS attacks. Google offer Cloud Armor, Azure offer Azure Web Application Firewall and AWS offer AWS WAF
- Traffic Monitoring and Anomaly Detection: Employ traffic monitoring and anomaly detection systems to identify unusual traffic patterns that may indicate a DDoS attack in progress. Monitoring network traffic and system logs can help detect and respond to attacks promptly.
- Incident Response Planning: Develop a comprehensive incident response plan that includes steps for handling DDoS attacks. This plan should outline roles and responsibilities, communication procedures, and strategies for mitigating and recovering from DDoS incidents.
- Traffic Scrubbing: Consider leveraging third-party DDoS mitigation services that specialise in scrubbing and filtering DDoS
- Redundancy and Load Balancing: Design your cloud infrastructure with redundancy and load balancing mechanisms to distribute traffic across multiple servers or instances. This helps minimise the impact of DDoS attacks by spreading the load and ensuring high availability.
- Regular Testing and Preparedness: Conduct regular DDoS testing and simulations to evaluate the effectiveness of your mitigation strategies and preparedness. This allows you to identify any weaknesses in your defences and make necessary improvements.
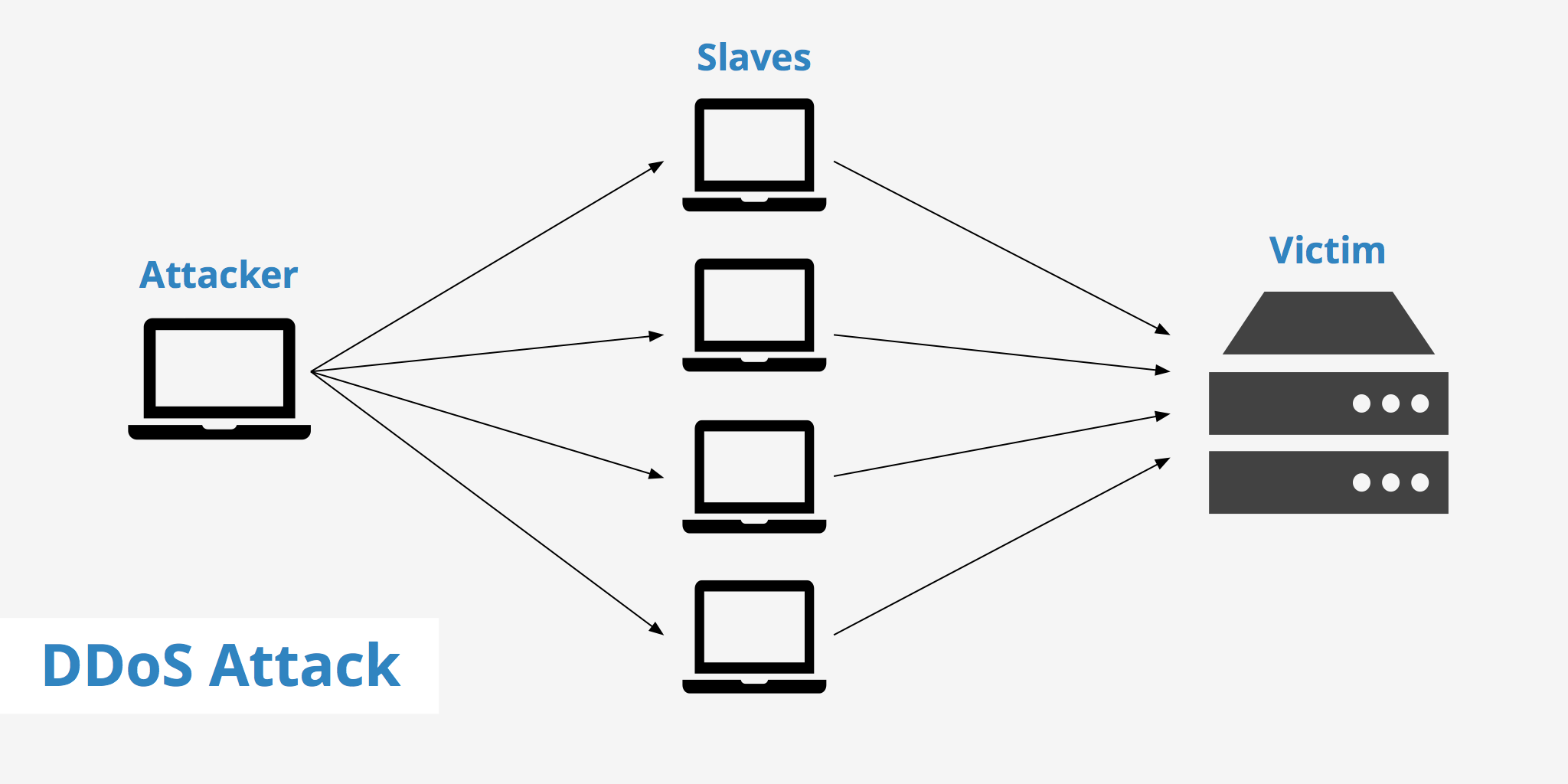
Source: KeyCDN
Security Advisory Notifications and essential contacts
It's important to make sure that when known issues are detected that the right people are informed. Make sure that you are able to get any information which your Cloud provider has available sent to people who can effectively do something about it. The Advisory Notifications Service is a feature provided by Google Cloud that delivers targeted communications regarding critical security and privacy events. It aims to provide timely and relevant information to organisations using Google Cloud services, helping them prioritise and respond effectively to potential threats or vulnerabilities.
- Advisory Notifications Service (ANS) delivers targeted communications about critical security and privacy events in the Google Cloud console.
- ANS is an important tool to help your organisation prioritise responses to critical security and privacy events.
- ANS is be gradually being enabled for all Google organisations and Mesoform can help you with the necessary integration of essential contacts and secure data management.
The Future of Cloud Security: Trends and Predictions
Finishing off, let's have a look forward to some concepts which we believe will be an big part of the future of cloud security - trends and predictions that will shape the way organisations protect their valuable data and assets. With the continued growth of cloud adoption and the evolving threat landscape, it becomes crucial to stay informed about the emerging practices and technologies in cloud security.
Below are some predictions and areas which Mesoform are either actively working on or investigating how the best practices around implementing for our clients
- Zero Trust Architecture (ZTA): Organisations will increasingly adopt ZTA, implementing stringent access controls, multi-factor authentication, and continuous monitoring to verify and authenticate users and devices accessing cloud resources.
- Container Security: As containerisation and micro-services gain popularity, organisations will prioritise securing containerised environments through tools and practices such as vulnerability scanning, image verification, and runtime protection.
- Cloud-Native Security Solutions: Dedicated security solutions tailored for cloud-native technologies like serverless computing will emerge, offering enhanced visibility, threat detection, and protection specific to cloud-native architectures.
- AI-Powered Threat Detection: Artificial intelligence (AI) and machine learning (ML) will be extensively utilised to detect and respond to sophisticated threats. AI-powered security tools will analyse vast amounts of data to identify patterns, anomalies, and potential breaches in real-time.
- Data Privacy and Compliance: Growing concerns about data privacy will drive stricter compliance regulations. Organisations will focus on robust data protection, encryption, and privacy measures to meet evolving regional and industry-specific requirements.
- Cloud Security Posture Management (CSPM): The adoption of CSPM tools will increase as organisations seek to continuously assess and enhance their cloud security posture. CSPM solutions offer automated security checks, configuration monitoring, and compliance assessments to identify and address vulnerabilities in cloud environments.
- Secure DevOps (DevSecOps): The integration of security into DevOps practices will gain further momentum, leading to the widespread adoption of DevSecOps. Security will be embedded throughout the development lifecycle, enabling early vulnerability identification and bolstering overall cloud security.
- Quantum-Safe Encryption: With the rise of quantum computing, the need for quantum-safe encryption will become paramount. Organisations will explore and adopt encryption methods capable of withstanding attacks from quantum computers, ensuring long-term data security.
- Cloud Security Service Providers: Specialised cloud security service providers will play an essential role as cloud security complexities grow. These providers will offer expertise in managing and securing cloud environments, delivering dedicated security teams, threat intelligence, and around-the-clock monitoring.
- Enhanced Cloud Security Collaboration: Industry collaboration and threat intelligence sharing will intensify. Organisations, cloud service providers, and security vendors will collaborate to address emerging threats, exchange best practices, and develop standardised security frameworks for cloud environments.
While these predictions provide insights into the future of cloud security, it's important to note that the cybersecurity landscape is ever-evolving. Organisations must remain agile and proactive in adopting emerging technologies and practices to stay ahead of potential threats and protect their cloud-based assets.
Source: TechVidvan

Mesoform offers secure deployments and training for our clients at a lower overall development cost due to our extensive experience in enterprise-grade Cloud security
If you would like to discuss any of these topics in more detail, please feel free to get in touch


